Azure Log In: 7 Ultimate Tips for a Secure & Fast Access
Logging into Azure doesn’t have to be complicated. Whether you’re a cloud beginner or an IT pro, mastering the azure log in process is your first step toward seamless cloud management. Let’s break it down—simply, securely, and smartly.
Azure Log In: Understanding the Basics

The azure log in process is the gateway to Microsoft’s powerful cloud ecosystem. Millions of users access Azure daily for virtual machines, storage, AI tools, and enterprise applications. But before diving into services, you need to understand how logging in works and why it matters.
What Is Azure Log In?
The term azure log in refers to the authentication process that grants users access to the Microsoft Azure portal, CLI, SDKs, or APIs. This process verifies your identity using credentials like email, password, and often multi-factor authentication (MFA).
Unlike traditional login systems, Azure leverages Azure Active Directory (Azure AD), a cloud-based identity and access management service. This means your login isn’t just about accessing a dashboard—it’s about secure identity governance across hybrid and cloud environments.
- Azure log in supports personal Microsoft accounts and work/school accounts.
- It integrates with on-premises directories via Azure AD Connect.
- Login can occur through web, mobile, or command-line interfaces.
“Authentication is the foundation of cloud security. A secure azure log in is the first line of defense.” — Microsoft Security Best Practices
Why Azure Log In Is Different from Regular Logins
Standard website logins often rely on username and password alone. Azure, however, operates in a zero-trust environment where identity is the new perimeter. This means the azure log in process includes advanced features like conditional access, risk-based policies, and device compliance checks.
For example, even if you enter the correct password, Azure might block access if the login attempt comes from an unfamiliar location or an unmanaged device. This level of control is what sets Azure apart from conventional systems.
Additionally, Azure supports federated identity providers like SAML and OAuth 2.0, allowing organizations to use existing identity systems (e.g., AD FS or third-party IdPs) instead of creating new credentials.
Step-by-Step Guide to Azure Log In
Whether you’re accessing Azure for the first time or troubleshooting a failed login, following a structured approach ensures success. Here’s how to perform an azure log in correctly and efficiently.
How to Log In to Azure via Web Portal
The most common way to perform an azure log in is through the official Azure portal at portal.azure.com. Follow these steps:
- Open a modern browser (Chrome, Edge, Firefox).
- Navigate to https://portal.azure.com.
- Enter your email address (e.g., user@company.com or user@outlook.com).
- Click ‘Next’ and enter your password.
- If enabled, complete multi-factor authentication (MFA).
- Upon verification, you’ll be redirected to the Azure dashboard.
After logging in, you’ll see the Azure homepage with access to resources, cost management, and service health. If you have multiple subscriptions, ensure you’re in the correct context using the subscription filter at the top.
Troubleshooting Common Azure Log In Issues
Even with the right credentials, users often face issues during the azure log in process. Here are the most frequent problems and their solutions:
“User not found” error: Ensure you’re using the correct email.Some users have multiple Microsoft accounts and may be logging in with the wrong one.”Password incorrect” despite correct entry: Check caps lock, keyboard layout, or try resetting the password via the ‘Forgot password?’ link.MFA not working: If using Microsoft Authenticator, ensure time sync is enabled.For SMS-based MFA, verify your phone number is up to date.Account locked: After multiple failed attempts, Azure may temporarily lock the account..
Wait 15–30 minutes or contact your administrator.For enterprise users, login issues may stem from conditional access policies.For example, a policy might require a compliant device or block access from certain countries.In such cases, contact your IT admin to review Azure AD policies..
Tip: Use InPrivate or Incognito mode to rule out browser cache or extension conflicts during azure log in.
Security Best Practices for Azure Log In
Securing the azure log in process is critical. A compromised account can lead to data breaches, unauthorized resource creation, or crypto-mining attacks. Implementing robust security measures protects both individuals and organizations.
Enable Multi-Factor Authentication (MFA)
MFA is one of the most effective ways to secure your azure log in. It requires users to verify their identity using two or more methods:
- Something you know (password)
- Something you have (phone, token)
- Something you are (biometrics)
Microsoft reports that MFA blocks over 99.9% of account compromise attacks. To enable MFA:
- Sign in to the Azure portal.
- Go to Azure Active Directory > Security > Multifactor Authentication.
- Select users and enable MFA.
For better user experience, consider using the Microsoft Authenticator app, which supports push notifications and passwordless login.
Use Conditional Access Policies
Conditional Access is a core feature of Azure AD that allows admins to enforce access controls based on specific conditions. For example, you can configure policies that:
- Require MFA when accessing from outside the corporate network.
- Block access from high-risk countries.
- Allow access only from compliant or hybrid Azure AD-joined devices.
To set up a Conditional Access policy:
- Navigate to Azure AD > Security > Conditional Access.
- Click ‘New policy’ and define conditions (e.g., user, location, device).
- Set access controls (e.g., require MFA, block access).
- Enable the policy and assign users.
These policies ensure that even if credentials are stolen, attackers can’t bypass security checks during the azure log in process.
“Conditional Access turns identity into a smart gatekeeper.” — Microsoft Azure Documentation
Advanced Azure Log In Methods
Beyond the standard web login, Azure supports several advanced authentication methods for developers, administrators, and automated systems. These methods enhance security and streamline access across environments.
Using Azure CLI for Log In
The Azure Command-Line Interface (CLI) allows users to manage Azure resources via terminal commands. To perform an azure log in using CLI:
- Install Azure CLI from Microsoft’s official site.
- Open your terminal (PowerShell, Bash, etc.).
- Run the command:
az login. - A browser window will open prompting you to authenticate.
- After successful login, the CLI displays your subscriptions.
For automation scripts, use service principals or managed identities instead of interactive login. This avoids storing credentials in code.
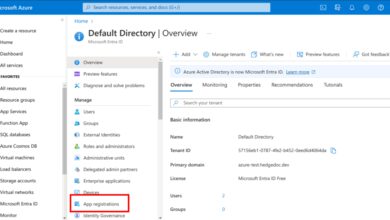
Service Principals and App Registrations
A service principal is an identity created for applications, services, or automation tools to access Azure resources without human intervention. It’s essential for secure azure log in in CI/CD pipelines or backend services.
To create a service principal:
- Go to Azure AD > App registrations > New registration.
- Enter a name and select supported account types.
- After registration, go to Certificates & secrets to generate a client secret.
- Assign roles via Role-Based Access Control (RBAC).
Once created, applications can use the client ID, tenant ID, and secret to authenticate programmatically. This method is far more secure than using personal credentials in scripts.
Passwordless Authentication for Azure Log In
Passwordless authentication is the future of secure access. Microsoft is actively promoting passwordless options to reduce phishing and credential theft during the azure log in process.
Microsoft Authenticator App
The Microsoft Authenticator app allows users to log in without entering a password. Instead, they receive a push notification and approve the login with a tap.
To set it up:
- Download the app on iOS or Android.
- In the Azure portal, go to Security Info under your profile.
- Add Microsoft Authenticator as a sign-in method.
- Scan the QR code with the app.
Now, when you perform an azure log in, you’ll receive a notification instead of entering a password. This method is faster and more secure.
FIDO2 Security Keys
FIDO2 keys (like YubiKey) provide phishing-resistant authentication. They use public-key cryptography instead of passwords.
To use a FIDO2 key for azure log in:
- Go to My Security Info in your account.
- Select Add method > Security Key.
- Insert the key and follow the prompts.
After setup, the key becomes your primary authentication method. No password needed—just insert the key and tap it when prompted.
“Passwordless isn’t just convenient—it’s a security revolution.” — Microsoft Identity Team
Managing Multiple Azure Accounts and Subscriptions
Many users manage multiple Azure accounts—personal, work, and client subscriptions. Navigating between them requires understanding how the azure log in system handles context switching.
Switching Between Azure Subscriptions
After logging in, you might have access to multiple subscriptions. To switch:
- In the Azure portal, click your account name in the top-right corner.
- Select Switch directory or Change directory.
- Choose the desired subscription or tenant.
In Azure CLI, use: az account set --subscription <subscription-id>
It’s crucial to verify your active subscription before deploying resources to avoid billing errors.
Using Azure Account Switcher
The Azure Account Switcher is a browser extension that simplifies managing multiple identities. It allows you to:
- Store multiple Azure accounts.
- Switch between them with one click.
- View active subscriptions and tenants.
This tool is especially useful for consultants or MSPs managing client environments. It eliminates the need to log out and back in repeatedly.
Monitoring and Auditing Azure Log In Activity
Security doesn’t end at login. Monitoring azure log in attempts helps detect suspicious behavior and ensures compliance.
Using Azure Sign-In Logs
Azure AD provides detailed sign-in logs that record every azure log in attempt. To access them:
- Go to Azure AD > Monitoring > Sign-in logs.
- Filter by user, app, status, or time range.
- Review details like IP address, location, device, and authentication methods.
Look for red flags such as:
- Logins from unusual countries.
- Multiple failed attempts.
- Access from anonymous IP addresses (e.g., Tor).
These logs are essential for incident response and forensic analysis.
Enabling Azure AD Audit Logs
Audit logs track administrative actions, such as role assignments or policy changes. While sign-in logs focus on authentication, audit logs show what users did after logging in.
To view audit logs:
- Navigate to Azure AD > Monitoring > Audit logs.
- Filter by activity, date, or user.
For long-term retention, export logs to Azure Monitor, Log Analytics, or a SIEM tool like Microsoft Sentinel.
“Visibility into login activity is non-negotiable for cloud security.” — Azure Security Benchmark
Common Azure Log In Scenarios and Solutions
Different roles require different login approaches. Understanding these scenarios ensures smooth and secure access.
Guest User Access and B2B Collaboration
Azure supports Business-to-Business (B2B) collaboration, allowing external users to access resources securely. When a guest user performs an azure log in, they use their home tenant’s credentials.
To invite a guest user:
- Go to Azure AD > Users > New guest user.
- Enter their email and send an invitation.
- They’ll receive a link to access resources after accepting.
The guest logs in through their own organization’s identity provider, reducing the need for password sharing.
Admin vs. User Log In Experience
Administrators have elevated privileges and thus face stricter login requirements. They often must:
- Use MFA at every login (no remember MFA option).
- Access resources through Privileged Identity Management (PIM).
- Justify access requests with a business reason.
PIM enables just-in-time (JIT) access, meaning admins aren’t permanently assigned high-privilege roles. They activate them when needed, reducing the attack surface.
Regular users, on the other hand, may have simpler login flows unless restricted by policy.
How do I reset my Azure password?
If you’ve forgotten your password, go to passwordreset.microsoftonline.com, enter your email, and follow the steps to reset it. You’ll need access to your recovery email, phone, or authenticator app.
Can I use the same Microsoft account for personal and Azure access?
Yes, you can use a personal Microsoft account (e.g., @outlook.com) to log in to Azure, but for enterprise use, it’s recommended to use a work or school account managed by Azure AD for better control and security.
Why am I getting a ‘No subscriptions found’ error after azure log in?
This means your account doesn’t have access to any Azure subscriptions. Contact your administrator to assign you a role like Reader or Contributor on a subscription.
Is there a way to automate azure log in for scripts?
Yes, use service principals or managed identities for automation. Avoid storing passwords in scripts. Use az login --service-principal with client credentials for CLI automation.
What should I do if my azure log in is blocked due to security risks?
Check if your IP or device is flagged. Try logging in from a trusted network or device. If the issue persists, contact your Azure administrator to review risk policies or clear the risk detection.
Mastering the azure log in process is essential for anyone using Microsoft’s cloud platform. From basic web access to advanced passwordless and automated logins, security and usability go hand in hand. By enabling MFA, using conditional access, monitoring sign-in logs, and adopting modern authentication methods, you can ensure secure and efficient access to Azure resources. Whether you’re an admin, developer, or guest user, a well-managed login experience enhances productivity and protects your cloud environment.
Recommended for you 👇
Further Reading: